
Introduction:
In today’s world, cyber threats are a growing concern for businesses of all sizes. As technology advances, so do the methods used by malicious actors to exploit vulnerabilities and compromise systems. In order to protect themselves, businesses need to have a strong cybersecurity strategy in place. One key component of any cybersecurity strategy is a Security Operations Center (SOC). In 2023, SOCs will play an even more important role in protecting businesses from cyber threats. The threat landscape is constantly evolving, and SOCs need to be able to keep up with the latest threats in order to protect their organizations. SOCs also need to be able to scale to meet the needs of their growing businesses.
What is SOC ?
A security operations center (SOC) is a centralized team of security professionals responsible for monitoring, detecting, and responding to cyber threats. SOCs use a variety of tools and techniques to collect and analyze data, identify potential threats, and take action to mitigate them. In simple terms Imagine a vigilant guardian constantly watching over your digital kingdom, ready to tackle any intruders. That’s precisely what a SOC does for your cybersecurity as a centralized command center. Its mission? To
monitor, detect, analyze, and respond to potential cyber threats promptly.
Why do you need a SOC in Cybersecurity?
In today’s world, cyber threats are more prevalent than ever before. Hackers are constantly looking for new ways to exploit vulnerabilities in computer systems and networks. A SOC can help you protect your organization from these threats by providing 24/7 monitoring and response services. With growing cyber-attacks in complexity and frequency, relying solely on traditional security measures is like leaving your front door unlocked. A SOC offers numerous benefits that enhance your security posture:
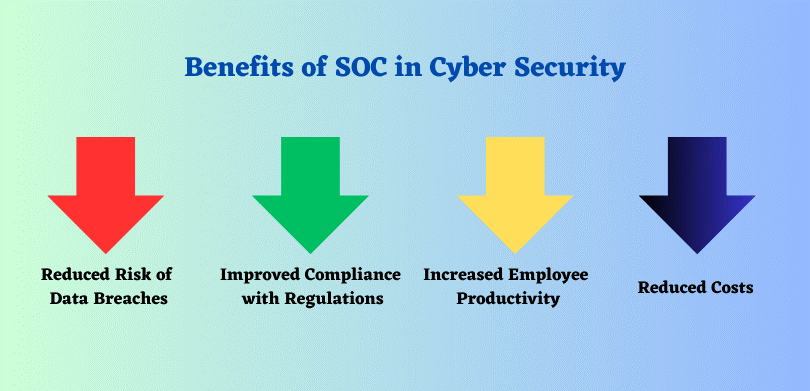
- Reduced Risk of Data Breaches:
Data breaches can have severe consequences, including financial losses, reputational damage, and legal implications. A SOC plays a pivotal role in minimizing the risk of data breaches. Through constant monitoring and threat detection, the SOC team can identify and mitigate potential threats before they escalate into significant security incidents.
- Improved Compliance with Regulations:
In today’s regulatory landscape, organizations are subject to various data protection and privacy regulations. Failure to comply with these regulations can lead to severe penalties and legal repercussions. A SOC aids in maintaining compliance by implementing robust security measures, monitoring for potential breaches, and promptly addressing any vulnerabilities or non-compliance issues.
- Increased Employee Productivity:
Cybersecurity incidents can disrupt business operations, leading to downtime and decreased productivity. A SOC’s proactive approach reduces the impact of security incidents, minimizing the disruption to your employees’ workflow. By swiftly containing and resolving security issues, the SOC helps maintain a stable and secure environment for your workforce
- Reduced Cost:
While establishing and maintaining a SOC involves investment, it can ultimately result in significant cost savings. The early detection and prevention of cyber threats by a SOC can prevent costly data breaches or system compromises. The expenses associated with incident response, remediation, regulatory fines, legal disputes, and reputational damage can far outweigh the investment in a SOC. Moreover, outsourcing SOC capabilities to Managed Security Service Providers (MSSPs) can be a cost-effective option, providing access to expert personnel, advanced technologies, and 24/7 monitoring at a fraction of the cost of building an in-house SOC.
How do I get a SOC ?
There are a few different ways to get a SOC. You can:
- Build your own SOC
- Outsource your SOC to a third-party vendor
- Use a managed security service provider (MSSP)
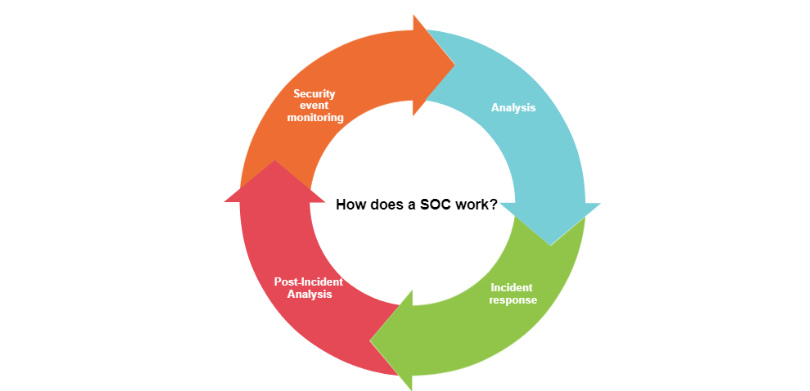
How does a SOC work in Cybersecurity ?
Think of a SOC as a detective agency devoted to sniffing out and thwarting cybercrime The specific tasks performed by a SOC will vary depending on the size and complexity of the organization it serves. However, most SOCs will perform the following functions:
- Security event monitoring: SOCs use a variety of tools to monitor network traffic, system logs, and user activity for signs of malicious activity. This includes looking for unusual patterns of behavior, such as repeated failed login attempts or excessive data transfer.
- Analysis: Once a potential threat is identified, the SOC team investigates its nature, severity, and potential impact on your systems. They dissect the attack, understanding its tactics, techniques, and motives.
- Incident response: When a SOC detects a security incident, they will take steps to contain the incident and mitigate the damage. This may include isolating the affected systems, removing malware, and notifying affected users.
- Post-Incident Analysis: A crucial step often overlooked is analyzing the incident thoroughly. The SOC team investigates the attack’s root cause, identifies vulnerabilities, and implements measures to prevent future occurrences.
How do SOC and Managed Security Services work ?
SOCs often work in conjunction with Managed Security Service Providers (MSSPs). These dedicated security firms offer SOC-as-a-Service (SOCaaS) to organizations, providing access to their expert teams, infrastructure, and technologies. This partnership allows businesses to leverage industry expertise without incurring the costs of building an in-house SOC.
Challenges of having a SOC in 2023:
- Cost: Setting up and maintaining a SOC can be expensive. You will need to purchase security tools, hire and train security professionals, and pay for ongoing maintenance and support.
- Staffing: SOCs require qualified security professionals with the skills and experience to identify and respond to cyber threats. These professionals can be difficult to find and hire, and they can be expensive to retain.
- Keeping up with the latest threats: The threat landscape is constantly changing, so SOCs need to be able to keep up with the latest threats. This requires investing in new security tools and training security professionals on new threats.
- Responding to security incidents quickly and effectively: SOCs need to be able to respond to security incidents quickly and effectively. This requires having a plan in place for responding to incidents, and having the resources and expertise to carry out the plan.
How to Improve your SOC with Cybersecurity in New Era:
- Invest in the latest technology: SOCs need to have the latest security tools in order to monitor and detect cyber threats. Investing in new security tools can help SOCs to improve their ability to identify and respond to threats.
- Train your employees on cybersecurity best practices: Employees are often the first line of defense against cyber threats. Training employees on cybersecurity best practices can help them to identify and report suspicious activity, and to protect themselves from phishing attacks and other social engineering techniques.
- Communicate with your employees about security risks: Employees need to be aware of the security risks that their organization faces. Communicating with employees about security risks can help them to understand the importance of following security best practices.
- Have a plan for responding to security incidents: SOCs need to have a plan in place for responding to security incidents. This plan should include steps for identifying and containing the incident, as well as steps for notifying affected employees and customers.

The Future of SOC in New Era:
As technology advances and cyber threats evolve, the SOC landscape is constantly evolving too. Here are a couple of exciting trends to keep an eye on:
- AI in SOCs: AI can be used to automate a variety of tasks in SOCs, such as data collection, analysis, and reporting. This can free up SOC analysts to focus on more complex tasks, such as investigating incidents and developing new security strategies. AI can also be used to improve detection rates by identifying potential threats that would otherwise go unnoticed. For example, AI can be used to analyze large amounts of data to identify patterns that may indicate malicious activity.
- Cloud-native SOC: Cloud-native SOCs are built on cloud-based infrastructure, which offers a number of advantages over traditional on-premises SOCs. These advantages include scalability, flexibility, and ease of integration with other cloud-based security solutions. Cloud-native SOCs can also be more cost-effective than traditional SOCs, as they do not require the same level of hardware and software investment.
Overall in the SOC, two significant trends, namely AI integration and the rise of cloud-native architectures, are paving the way for the future. These trends bring forth a multitude of benefits, empowering organizations to enhance their security defenses and mitigate the risk of cyberattacks.
Conclusion:
SOC is an important part of any organization’s cybersecurity strategy. By monitoring, detecting, and responding to cyber threats, SOCs can help protect your organization from a variety of risks. If you don’t have a SOC, now is the time to consider getting one. A well-implemented SOC, supported by skilled professionals, advanced technology, and a proactive approach to cybersecurity, can significantly reduce the risk of data breaches, enhance compliance, and safeguard valuable assets. With a robust SOC in place, organizations can navigate the evolving threat landscape with confidence, ensuring a secure digital environment for their operations and stakeholders.



